Blog > When Fitness Trackers Exposed Military Secrets
David Herse | September 11, 2025
When Fitness Trackers Exposed Military Secrets
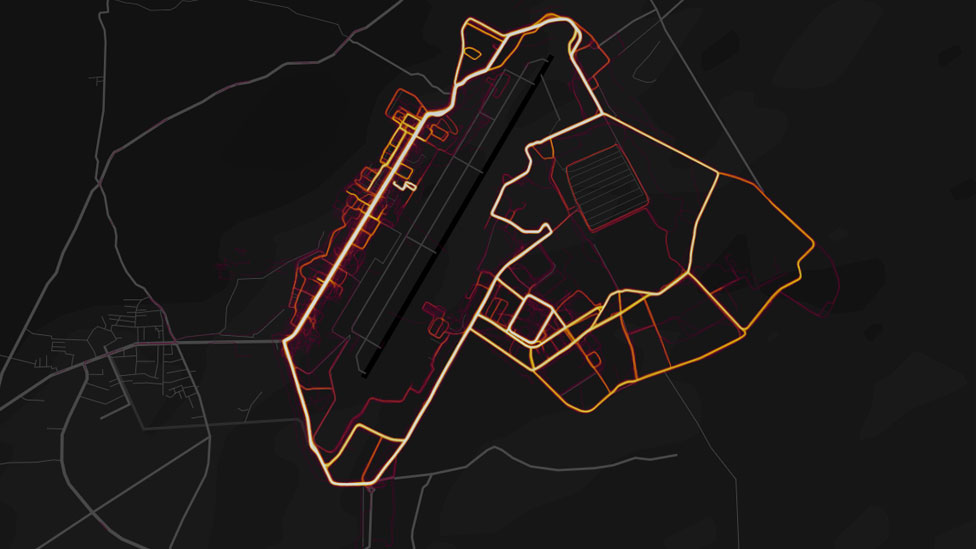
In January 2018, Australian researcher Nathan Ruser noticed something odd while browsing Strava’s new Global Heatmap. Jogging paths were glowing in the middle of the Syrian desert—right where U.S. and allied military bases were located.
The discovery quickly spread. Journalists confirmed that fitness tracker data was unintentionally exposing:
- Perimeters of foreign bases in Iraq, Afghanistan, and Syria
- Supply routes and patrol paths leading in and out of bases
- Patterns of life—how soldiers, contractors, and security staff moved daily
The U.S. Department of Defense soon launched a review, acknowledging that personal fitness data could endanger operations. Strava restricted some visibility settings in response.
The risk wasn’t a single jog—it was the aggregate movement patterns. Enough shared runs and rides could outline sensitive facilities or link work sites to residential addresses.
The Story Didn’t End in 2018
In 2024–25, French newspaper Le Monde revived the issue with its #StravaLeaks investigation. Reporters showed how publicly available Strava activities exposed:
- Members of President Macron’s security detail jogging near official residences and hotels
- Secret Service agents and other security personnel in the U.S. posting runs that risked revealing operational routines
- Military personnel in conflict zones—including Israeli soldiers near Gaza—whose fitness data mapped sensitive positions
The series underscored that even after earlier scandals, fitness app data was still leaking high-value intelligence.
Why It Matters
This is a classic case of open-source intelligence (OSINT): everyday consumer data becoming a national security vulnerability. It shows how:
- Seemingly harmless data can, when aggregated, reveal hidden infrastructure
- “Patterns of life” are often more revealing than one-off events
- Civilian platforms can unintentionally undermine military secrecy
As one U.S. official put it at the time, fitness apps were “the new geotagged photo”—a modern data exhaust that adversaries could exploit.
The Bigger Picture: Location Data as Intelligence
The Strava incidents highlight a fundamental challenge in our connected world: consumer technology generates intelligence-grade data. What starts as personal fitness tracking becomes, at scale, a global surveillance network.
For Military and Security Organizations
The implications are clear:
- Operational Security (OPSEC) must extend to personal devices
- Data hygiene is as important as physical security
- Aggregate patterns pose risks even when individual activities seem harmless
For Businesses and Civilians
The lessons apply beyond military contexts:
- Executive Protection: CEO running routes can reveal home addresses and routines
- Corporate Espionage: Employee movement patterns can expose R&D facilities or supplier relationships
- Personal Safety: Regular routes make individuals predictable and potentially vulnerable
What This Means for Location Intelligence
For those of us working with location data, the Strava story is both a cautionary tale and a demonstration of power. Location data reveals truth—sometimes uncomfortable truth—about how we live and work.
The Double-Edged Sword
Location intelligence platforms can:
- Reveal competitive insights through employee movement patterns
- Identify market opportunities via consumer behavior
- Optimise operations by understanding actual vs. planned routes
But they also require:
- Strict privacy controls to protect sensitive information
- Aggregation policies that prevent individual identification
- Clear data governance about what’s collected and shared
Lessons for Australian Organizations
Australian businesses and government agencies face unique challenges:
- Remote operations in mining and resources create isolated data signatures
- Small populations make anonymisation harder
- Strategic location means both allies and adversaries pay attention
Best Practices for Location Data
- Audit Your Digital Footprint
- What location data do your employees generate?
- Which apps and platforms have access?
- How might aggregated data reveal operations?
- Implement Data Policies
- Clear guidelines for fitness apps and social media
- Geofencing sensitive locations
- Regular training on data risks
- Use Professional Tools
- Consumer apps prioritize features over security
- Business platforms offer better controls
- Professional tools separate personal from operational data
The Ongoing Challenge
Years after the initial Strava revelations, the same vulnerabilities persist. New platforms emerge, each collecting location data in novel ways. The challenge isn’t just technical—it’s behavioral. How do we balance the benefits of connected technology with the risks of oversharing?
For military personnel, the answer might be strict device policies. For businesses, it’s about awareness and appropriate tools. For individuals, it’s understanding that convenience often comes at the cost of privacy.
Moving Forward: Responsible Location Intelligence
The Strava story doesn’t mean we should abandon location technology. Instead, it highlights the need for:
- Thoughtful implementation of location-based services
- Professional-grade tools for sensitive applications
- Ongoing education about data risks and benefits
Location data is powerful. The same patterns that exposed military bases can optimise supply chains, improve emergency response, and enhance customer service. The key is using this power responsibly.
Working with location data? Whether you’re protecting sensitive operations or leveraging location intelligence for business advantage, the right tools and policies matter. At Mapulus, we help Australian organizations harness location data securely and effectively.
Sources
- Ruser, Nathan. (2018). Twitter discovery of base exposures. Australian Strategic Policy Institute / AIIA.
- Sly, Liz. (2018, Jan 28). “U.S. soldiers are revealing sensitive and dangerous information by jogging.” Washington Post.
- ABC News – Strava heatmap shows military bases and supply routes
- Wired – Strava’s fitness app can reveal military sites
- ABC News – Pentagon reviewing security after Strava app reveals locations
- Engadget – After exposing military bases, Strava restricts data visibility
- Le Monde – #StravaLeaks investigative series (2024–25)
Note: This article is for educational purposes about data security and location intelligence. Always follow your organization’s security policies regarding location-sharing applications.